The following measures can help you protect yourself your employees and your users from phishing attacks. It also helps the security team react faster thanks to their reports.
 Phishing Protection Checklist How To Protect Yourself From Phishing
Phishing Protection Checklist How To Protect Yourself From Phishing
Here are some ways to recognize a phishing email.

How to protect against phishing. Ad Download Avast Free Antivirus and protect your PC against viruses and malware. These updates could give you critical protection against security threats. Get the Essential Free Protection That Wont Let You Down.
How to protect from phishing Enterprises seeking to safeguard systems and sensitive data from phishing attacks should ensure they educate their employees on signs to look for that may be suspicious. Dont open attachments or links in unsolicited emails even if the emails came from a recognized source. Empowering users to detect and report phishing attacks helps protect the organization no matter the type of phishing.
See Whos Our Best Rated Antivirus Software. Phishing attempts are so common now that youd be hard pressed to find an internet user who hasnt seen one. Learn the signs of a phishing scam The best protection is awareness and education.
Ad Download Avast Free Antivirus and protect your PC against viruses and malware. Protect Your Computer From Viruses Malware. Be vigilant and pay attention.
Ad Block Unsafe Links Downloads Email Attachments with AVG Free Antivirus. According to the governments cyber breaches survey 86 of businesses experienced a phishing. Our best antivirus to keep your PC secure and private.
Ad 2021s Best Antivirus Review. Protect your accounts by using multi-factor authentication. Set the software to update automatically so it can deal with any new security threats.
Let Us Help You Find The Perfect Antivirus. Protect Your Computer From Viruses Malware. How do you protect against phishing attacks.
The best defense is awareness and knowing what to look for. How to help protect yourself against email phishing scams. Do not click any links or download any attachments in the suspicious email.
Four Steps to Protect Yourself From Phishing. If the email is unexpected be wary about opening the attachment and verify the URL. Often theyll claim you have to act now to claim a.
Let Us Help You Find The Perfect Antivirus. Get the Essential Free Protection That Wont Let You Down. Protect your mobile phone by setting software to update automatically.
Our best antivirus to keep your PC secure and private. Instead open up your web browser and go to the website in question by typing it into the URL bar. Urgent call to action or threats - Be suspicious of emails that claim you must click call or open an attachment immediately.
Ad Block Unsafe Links Downloads Email Attachments with AVG Free Antivirus. Ad 2021s Best Antivirus Review. Phishing tests can be carried out regularly judging.
See Whos Our Best Rated Antivirus Software. Protect your computer by using security software.
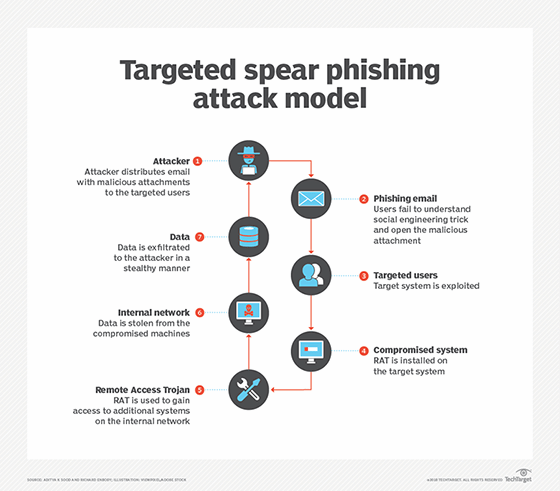 Phishing Protection Keep Employees From Getting Hooked
Phishing Protection Keep Employees From Getting Hooked
 How To Protect Yourself From Phishing Scams Norton Community
How To Protect Yourself From Phishing Scams Norton Community
 17 Phishing Prevention Tips Prevent Phishing Attacks Scams Email Threats Phishprotection Com
17 Phishing Prevention Tips Prevent Phishing Attacks Scams Email Threats Phishprotection Com
 The Complete Guide To Phishing Attacks Varonis Guide
The Complete Guide To Phishing Attacks Varonis Guide
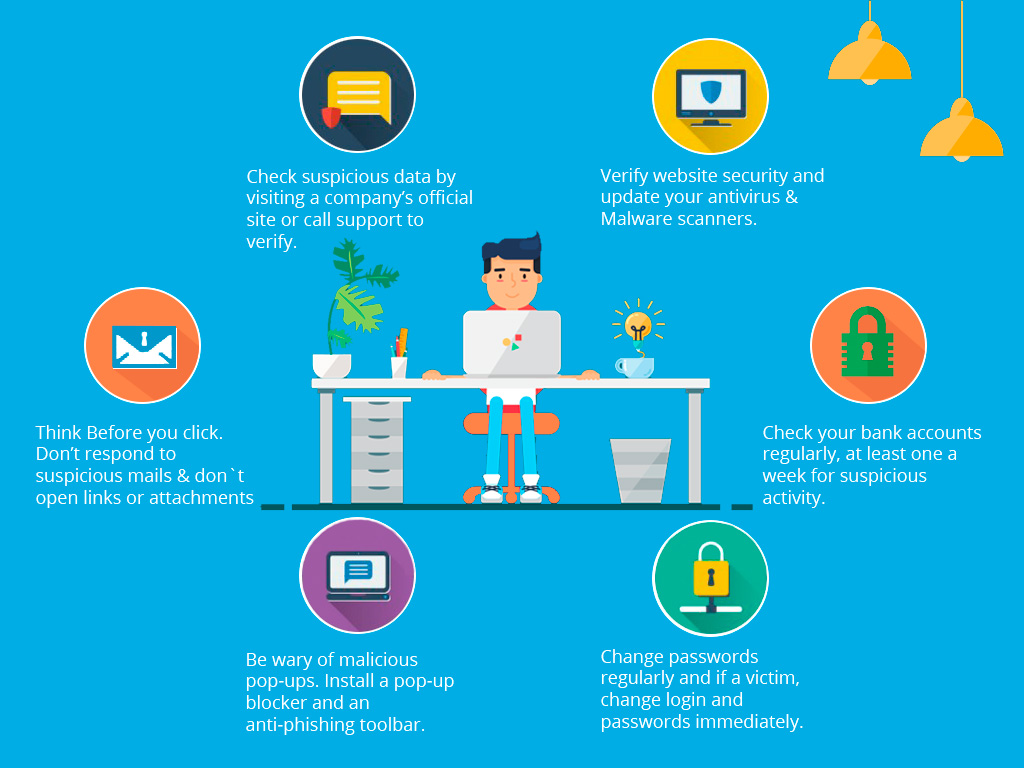 Email Security Protecting Yourself Against Phishing Scams Hosting Co Uk
Email Security Protecting Yourself Against Phishing Scams Hosting Co Uk
6 Common Phishing Attacks And How To Protect Against Them Ianoffers Com
 Phishing Protection Checklist How To Protect Yourself From Phishing
Phishing Protection Checklist How To Protect Yourself From Phishing
 10 Tips On How To Prevent Phishing Attacks On Your Personal Data
10 Tips On How To Prevent Phishing Attacks On Your Personal Data
 What Is A Whaling Attack Whale Phishing Prevent Examples
What Is A Whaling Attack Whale Phishing Prevent Examples
 Anti Phishing Services Phishing Solutions Protection Fraudwatch International
Anti Phishing Services Phishing Solutions Protection Fraudwatch International
 10 Tips On How To Prevent Phishing Attacks On Your Personal Data
10 Tips On How To Prevent Phishing Attacks On Your Personal Data
 10 Tips On How To Prevent Phishing Attacks On Your Personal Data
10 Tips On How To Prevent Phishing Attacks On Your Personal Data
 10 Ways To Protect Yourself From Phishing Attacks
10 Ways To Protect Yourself From Phishing Attacks
 10 Tips To Protect Yourself From Phishing Kaspersky Official Blog
10 Tips To Protect Yourself From Phishing Kaspersky Official Blog

No comments:
Post a Comment
Note: Only a member of this blog may post a comment.